 ICanProve digitally signed screenshots
ICanProve digitally signed screenshotsand session logs
 ICanProve digitally signed screenshots
ICanProve digitally signed screenshots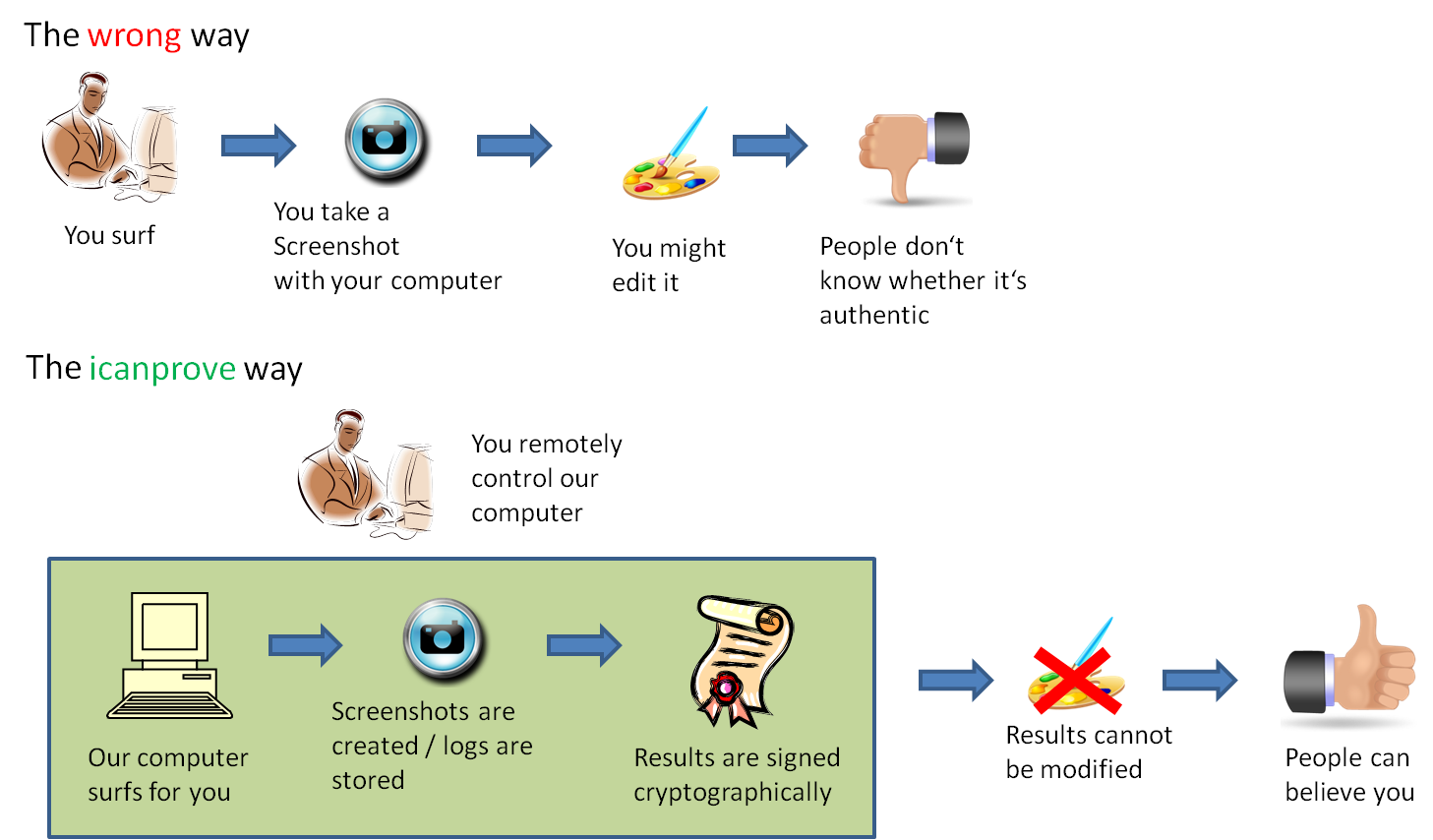

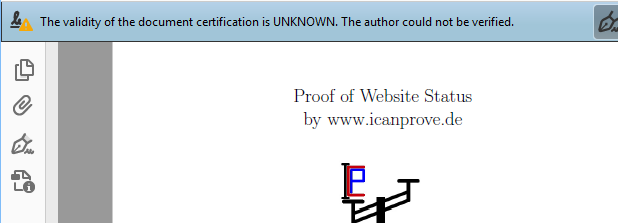
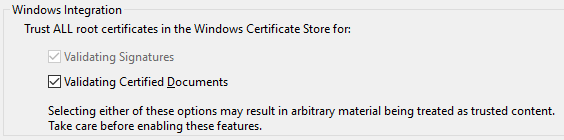
You should not. I have been very cautious and have implemented many security mechanisms, but every website can be hacked and furthermore you do not know me at all. So if you absolutely need to enter secret passwords please change them immediately afterwards. Never ever enter transaction codes.
